Устанавливаем Web Apps.
Переходим к настройке ssl.

Переходим к настройке ssl.
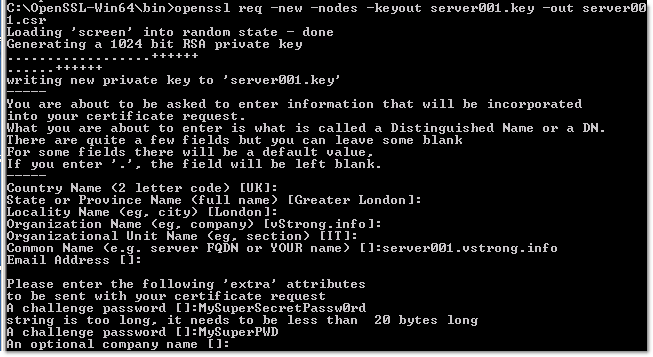
- Вызываем консоль mmc.exe, где выбираем оснастку сертификатов и тип сертификатов - учётной записи компьютера

- Правой клавишей на Certificates - Personal, где выбрать "Все задачи - Дополнительные операции - Создать настраиваемый запрос."

- Тип шаблона - Web Server, тип запроса - PKSC #10

- В политике автоматической выдачи сертификатов развернуть дополнительные сведения, где нажать Properties

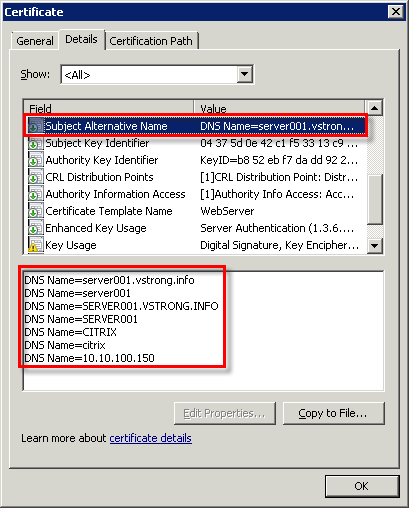
- На данном этапе необходимо знать, под какими именами OWAS будет опубликован в корпоративную сеть и в Интернет. Создать в Subject Name поле Common Name с Value = FQDN сервера - это важно! и нажать Add.
В Alternative Name создать поле DNS со значением №1 = FQDN сервера, значением №2 = имя публикации в Интернет. В данном примере, у меня, имена одинаковые, поэтому повторять нет смысла.
- На вкладке General вписать Friendly Name "Web Apps", чтобы потом не думать, что за сертификат.
- На вкладке Privat Key - Key options выбрать опцию Make this key exportable.

- Выбираем путь сохранения шаблона

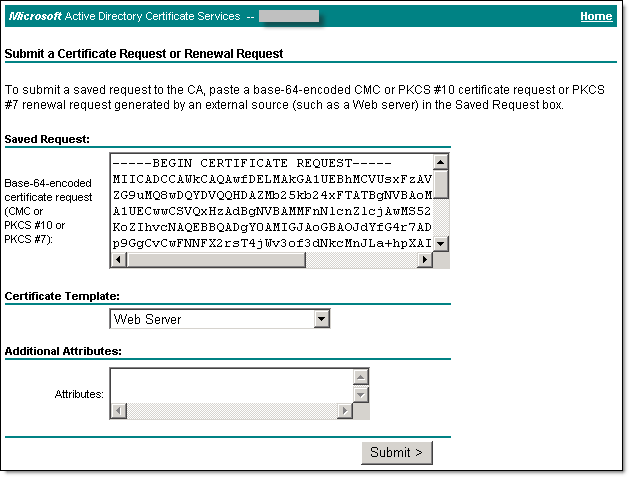
- Заходим на web-форму Центра Сертификации, где выбираем создание сертификата по запросу Base-64-encoded certificate request, шаблон Web Server, вставляем содержимое запроса в форму.

- Сохраняем сертификат на сервере.
- В консоли mmc на Certificates - Personal правой клавишей выбрать действие - Все задачи - Импорт

Настройка OWAS проводится из PowerShell, который необходимо запустить с правами администратора.
Загрузить модуль OWAS:
Запустить команду настройки фермы OWAS:
и согласиться на изменения.
Загрузить модуль OWAS:
Import-Module OfficeWebApps
Запустить команду настройки фермы OWAS:
New-OfficeWebAppsFarm -InternalUrl "https://wa01.domain.local" -ExternalUrl "https://wa01.domain.local" -CertificateName "Web Apps" -EditingEnabled
и согласиться на изменения.

В браузере зайти по адресу https://wa01.domain.local/hosting/discovery и увидеть xml-файл конфигурации сервера
Далее переходим на сервер Sharepoint
запустим SharePoint Management Shell выполним:
New-SPWOPIBinding -ServerName wa.lab.mars.ua
Убедимся что мы используем https:
Get-SPWOPIZone
Если наш сервис доступен только внутри сети включим использование internal-https:
Set-SPWOPIZone –zone “internal-https”
А если доступен “снаружи” то включим external-https:
Set-SPWOPIZone –zone “external-https”
http://www.unix.ck.ua/content/office-web-application-server-ustanovka-nastroika-sertifikatsiya
https://www.it-community.in.ua/2013/02/ustanovka-i-nastroyka-office-web-apps-v-sharepoint-2013.html/
https://www.it-community.in.ua/2013/02/ustanovka-i-nastroyka-office-web-apps-v-sharepoint-2013.html/